With the COVID-19 pandemic affecting all different types of businesses, the level of commitment each organization is ready to commit to is different. After assisting organizations with their efforts to put measures in place to safeguard staff and visitors since the coronavirus outbreak, Savance has taken this experience and categorized the approaches into three different categories.
Report (Level 1)
For the first tier, your objective is to replace paper logs with electronic ones and automate what might be very labor intensive and costly today. The system can alert someone if a person’s temperature is out of range or if they answer your configurable screening questions unfavorably. This is the most common COVID-19 screening approach and easy to implement.
- Electronic logs
- Contract tracing reports
- Kiosks with automated temperature checks
- Alerting when temp out of range or questions unacceptable
Alert (Level 2)
Beyond alerting that someone falls out of acceptable range, Level 2 ensures that if people access the building but have not yet screened, staff are immediately alerted that unscreened staff has entered the building. This is done by integrating with the access control system to monitor door event activity, and, upon receiving a door event, making sure that the person was screened within the past configurable amount of time. This prevents you from relying on trust or manually auditing the work schedules and cross-referencing those to the screening records.
- Same as Level 1
- Adds Access Control Integration
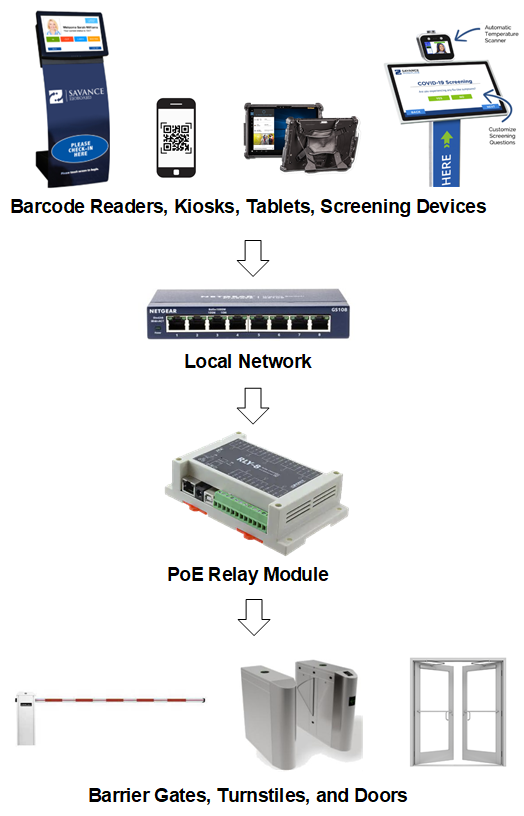
Prevention (Level 3)
For this level, your intention is to prevent access until the person is successfully screened for COVID-19. There are several different ways to accomplish this.
- Relay Module: The use of a relay module is the simplest way to prevent access. A relay is triggered on screening success or even failure. Typically, upon success, you either control an inside door or turnstile, or you allow power or communications from the reader to pass through the relay allowing normal reader operations to work for as long as the relay is held.
- Access Control Integration:
- Security Group Addition/Removal: After successfully screening, an API call to the access control system is called to add a person to a security group. After a set amount of time, a person is then removed from the same security group.
- Expiration Date Modification: After successfully screening, an API call to the access control system is made to extend the expiration date for X hours or Y days.
- Immediately Disable or Expire Credential: After unsuccessfully screening, an API call to the access control system is made to immediately expire or disable the credential.
- Something Unique: For example, send a Wiegand signal with the badge ID from a prox module so the access control system can handle it like anti-passback to disable the person’s credential.